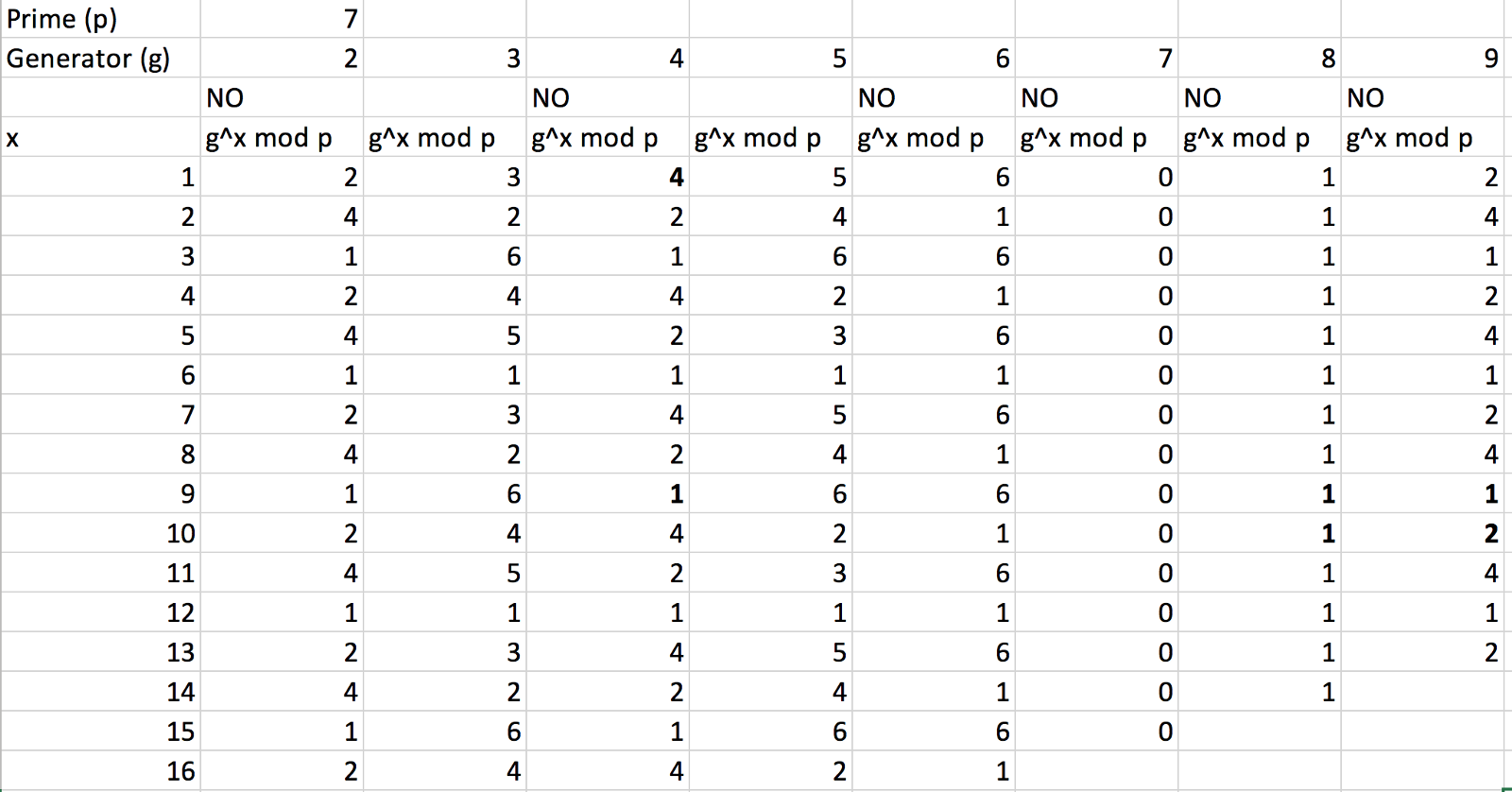
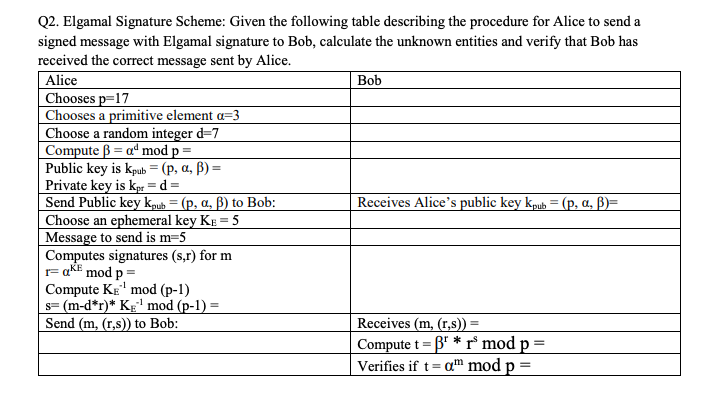
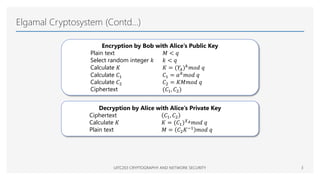
SOLVED: 10.0 We now consider the Elgamal signature scheme. You are given Bob'pri- vate key Kpr (d) = (67) and the corresponding public key Kpub (p,a,B) (97,23,15). [. Calculate the Elgamal signature (
Elgamal demonstration project on calculators TI-83+ Gerard Tel Utrecht University With results from Jos Roseboom and Meli Samikin. - ppt download

Key Calculation Time (in Milliseconds) by Proposed MR-PR Method, ECC,... | Download Scientific Diagram